A firewall is a security tool that restricts the number of ports on your machine through traffic can be sent to and received from other computers. When you use a firewall to restrict communication to a small number of ports, you can limit how your machines are accessible and ensure that only the programs you intend can be contacted by people outside your organization. For example, it is common to allow only web traffic to go through to a web server and prevent all other types of traffic. Firewalls can be implemented through hardware, software, or a combination of both.
Firewalls help to prevent some attacks, such as worms and some Trojan horses. These attacks enter or leave your system through open ports that are exposed by programs running on your machine but are not intended to be exposed to the open internet. Firewalls do not protect you from viruses attached to emails or from threats inside your network. Therefore, although firewalls are important, they should not be the only component of your overall security strategy. Antivirus software and solid authentication and authorization techniques are examples of other security strategies that should be deployed in conjunction with firewalls.
Note:
Firewalls that work by limiting open ports are different from web application firewalls, which actively work to analyze incoming web traffic and can block suspicious content. Web application firewalls can be beneficial tools in your overall security strategy but are not the focus of this topic.It's a security best practice to implement a perimeter network, also known as a demilitarized zone (DMZ) or screened subnetwork, to prevent external users from directly accessing your ArcGIS Server site. A perimeter network functions as the only exposed point in your network that is accessible to external users. It adds a layer of security to your organization's network.
This topic discusses the use of firewalls to protect stand-alone ArcGIS Server sites (those not federated with an ArcGIS Enterprise portal). To learn more about network security for the ArcGIS Enterprise portal and federated ArcGIS Server sites, see About securing your portal.
Protecting ArcGIS Server with firewalls
There are several appropriate strategies you can take to protect your stand-alone ArcGIS Server site with firewalls. The following strategies use firewalls to separate your internal network (in which security is regulated) from the external network (in which security cannot be guaranteed).
Multiple firewalls with reverse proxy and ArcGIS Web Adaptor in a perimeter network
If your organization does not yet use a reverse proxy server, you can configure it and ArcGIS Web Adaptor within a perimeter network. In this scenario, ArcGIS Web Adaptor receives incoming requests through port 443. It then sends the request through another firewall to ArcGIS Server, using port 6443. ArcGIS Web Adaptor causes the machine to act as a reverse proxy.
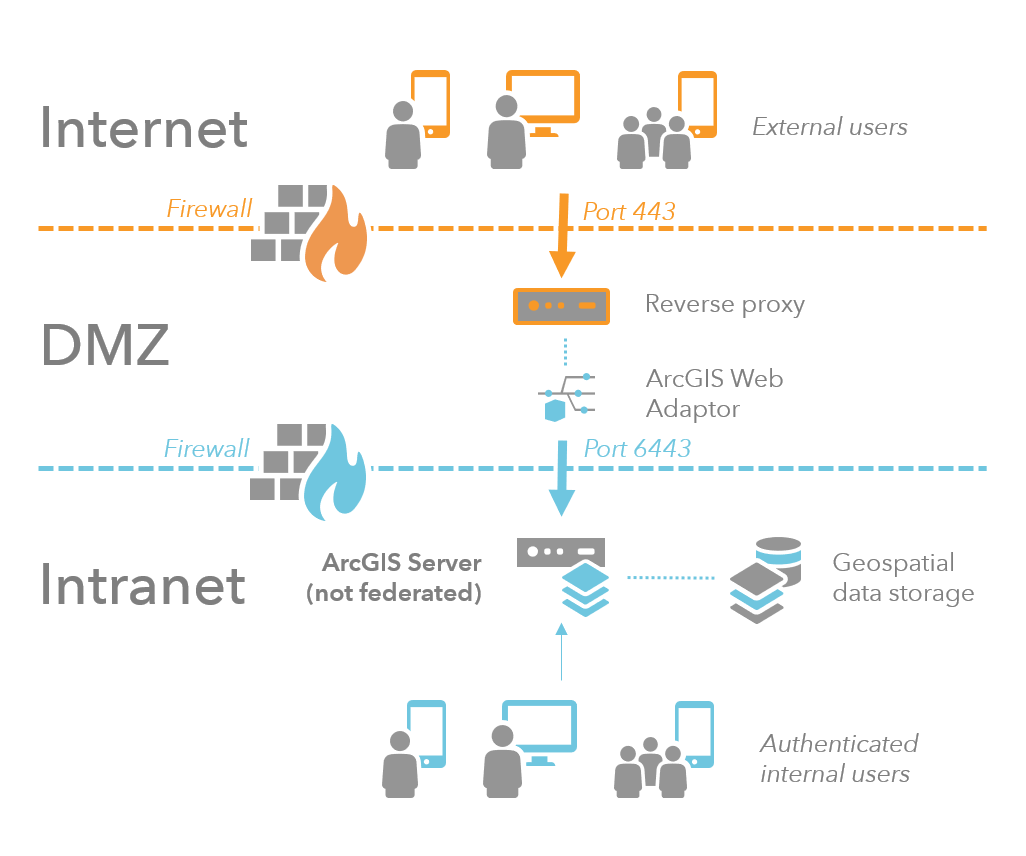
The following provides a closer look at each component in this scenario:
- A perimeter network consists of machines that internet users can access through a firewall but are not part of your secure internal network. The perimeter network isolates the internal network from direct internet client access.
- The ArcGIS Web Adaptor in the perimeter network receives internet requests through a common port, such as port 443. A firewall prevents access through any other ports. Then ArcGIS Web Adaptor sends the request to the secure internal network through another firewall using the ArcGIS Server port 6443.
- ArcGIS Server and other ArcGIS Enterprise components reside in the secure internal network. A request entering the secure network must come from ArcGIS Web Adaptor and pass through a firewall. A response leaving the secure network returns to the client the same way it arrived. First, the response passes back through the firewall to ArcGIS Web Adaptor. Then ArcGIS Web Adaptor sends it through another firewall to the client.
If a machine in the perimeter network somehow becomes compromised, the second firewall reduces the chance that the affected machine can harm machines in your internal network.
Integrating an existing reverse proxy
If your organization already uses a reverse proxy, you can configure it to route requests to ArcGIS Server on your secure internal network.
To ensure that the port between the reverse proxy and your secure internal network remains hidden from external users, install ArcGIS Web Adaptor on another web server within your secure internal network.
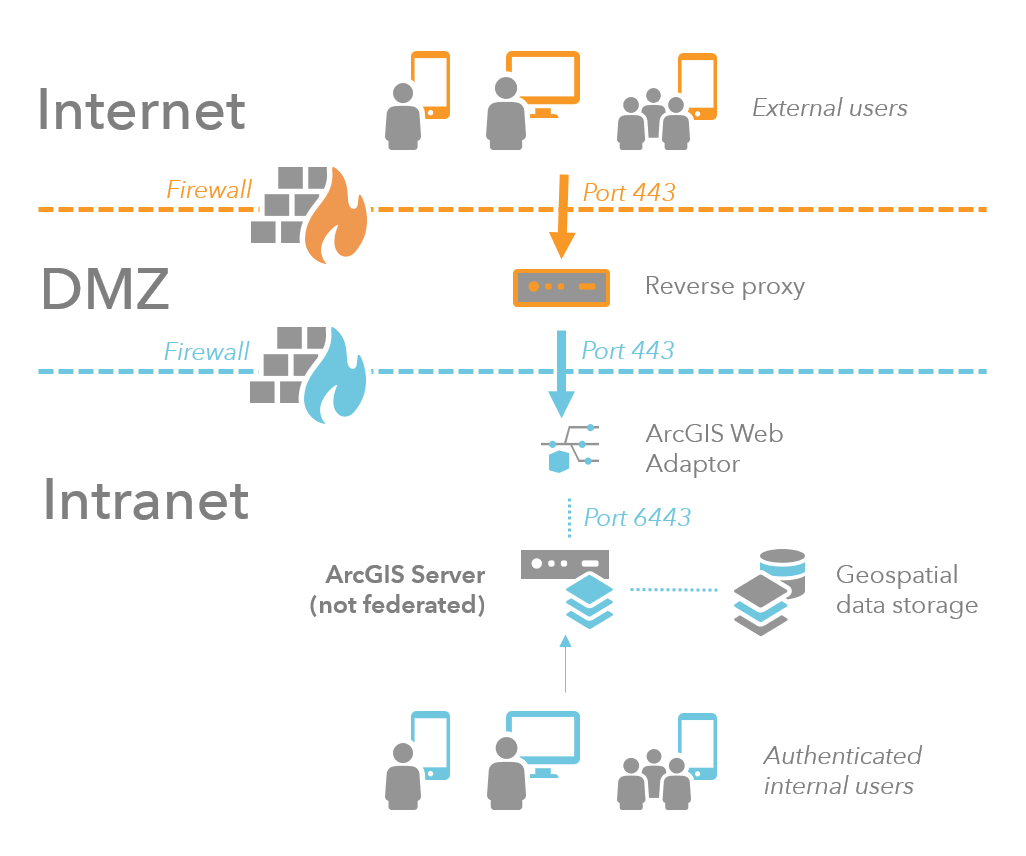
To learn more about how to integrate ArcGIS Server with your reverse proxy server, see Using a reverse proxy server with ArcGIS Server.
Single firewall
A less secure option uses a single firewall to restrict traffic to your web server. Usually, only port 443 is left open. Your web server, ArcGIS Web Adaptor, ArcGIS Server, and your data all reside behind the firewall in the secure internal network.
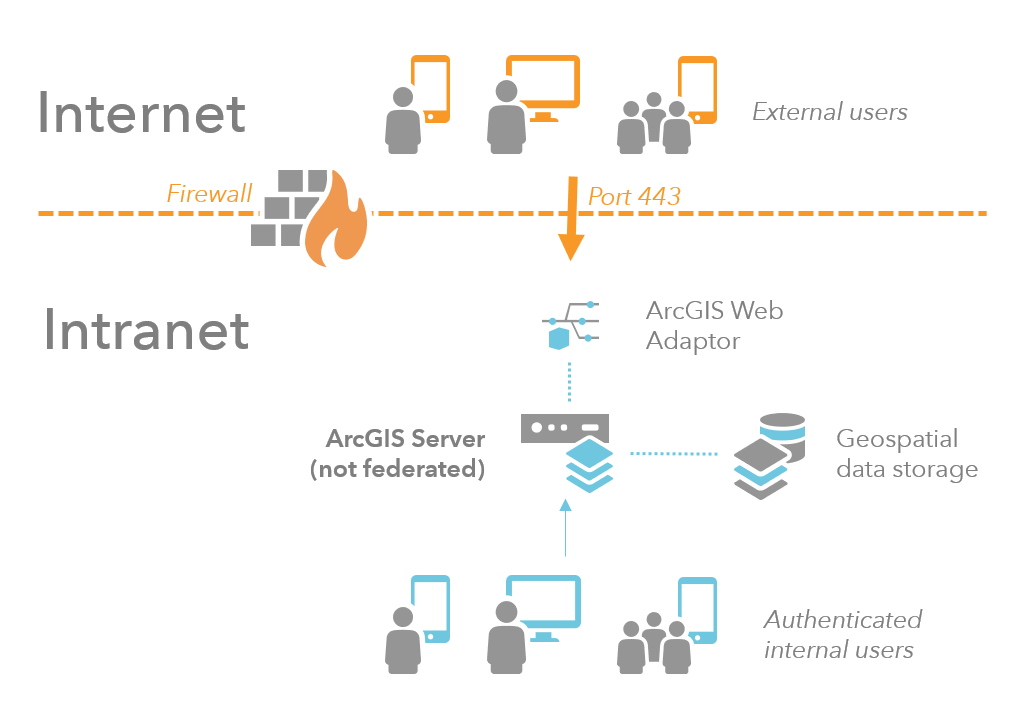
For robust network security, place multiple layers of defense between external clients and your internal network. If a single firewall is the only layer of defense, a breach of that layer opens your secure network to potential malicious activity. For this reason, this type of security configuration is not recommended.
Firewalls between ArcGIS Server machines
It's typically not necessary to place firewalls between the machines in an ArcGIS Server site or between multiple ArcGIS Server sites. However, if you do have firewalls between the machines, open the ports listed in Ports used by ArcGIS Server.